All businesses rely on BI tools to gather, measure, secure, and visualize data to identify trends and metrics. Business intelligence reports and dashboards help make these business decisions through a variety of data visualizations, tables, KPIs, and more.
Data security and governance play a significant role in deploying any business intelligence tool. Implementing role-based security with BI tools will ensure the appropriate people access the correct data and information across all verticals. Setting security roles keeps confidential information confidential. Role-based permissions allow admins to organize and funnel data to the appropriate users. These permissions streamline processes and ensure a smooth end-user experience.
For example, many BI reports and dashboards may not contain sensitive data, but it still may only be relevant to the company's individual stakeholders. Personnel in HR or finance would not need to access dashboards or reports focused on marketing campaigns or support metrics. In either case, data security and governance play a significant role in deploying any business intelligence tool, to control user access.
Wyn Enterprise offers a secured business intelligence environment with role-based permissions and control. Businesses of all sizes use business intelligence tools to gather, measure, secure, and visualize data. These tools help companies identify trends and metrics that inform data-driven decisions.
Here, we'll outline how to set up role-based permissions in your hosted instance of Wyn Enterprise.
Permissions Model For Data Security
Every organization groups its employees into specific roles or user groups, depending on their function in the business. These employees are then granted access rights to company systems, data, and other secured content in accordance to these user groups or roles.
Wyn's permissions model grants access privileges to different user roles, rather than to individual users. Role-based permissions decouple access control from document sharing. This model allows system administrators to control server load by restricting document creation to only authorized users. And those document authors can then share with others inside their roles. This process decreases the burden placed on system administrators to monitor who creates or shares documents.
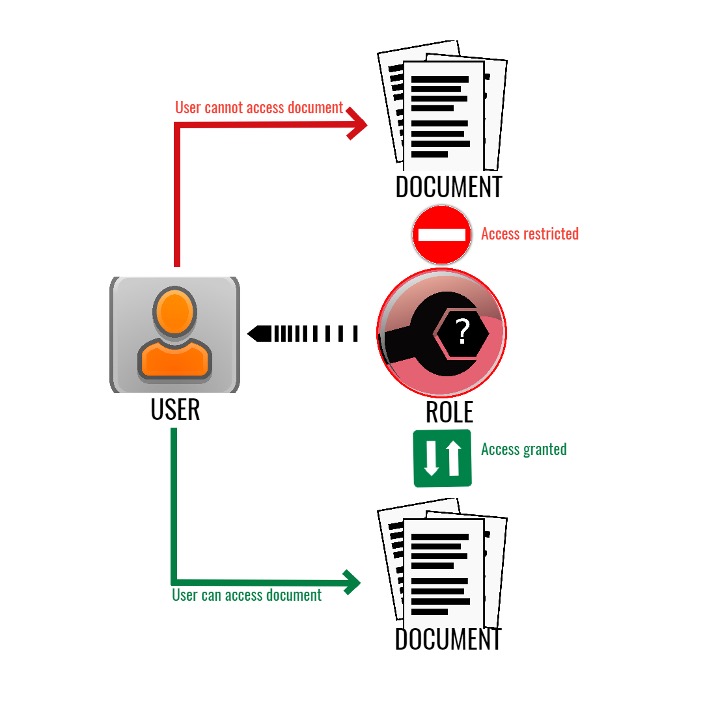
To set up role-based access control in Wyn Enterprise, follow these simple steps:
- Group Business Users
- Identify Responsibilities of Each Group
- Define and Create Roles
- Assign Permissions to Each Role
- Add Users to Defined Roles
- Share Documents and Resources
1. Group the Business Users
First, identify the users who will access Wyn and create groups based on business requirements. In typical setups, users belong to one or more roles.
The list of roles includes a variety of organizational functions, as shown below.
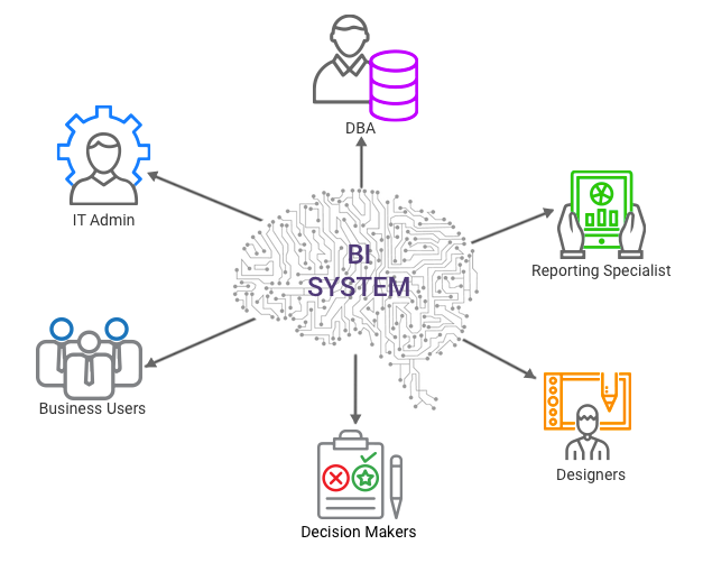
2. Identify Responsibilities of Each User Group
Once the groups are defined, decide what permissions to assign them. Workers should have access to the data they need to do their jobs. This step involves considering each user group and deciding on what permissions they need in Wyn Enterprise.
3. Define and Create Roles in Wyn Administrator Portal
Once you identify the appropriate user groups and their respective permissions, create roles for each group in Wyn's Administrator Portal.
Wyn provides two default roles: "administrator" and "everyone."
Anyone in the "administrator" role has full control of Wyn Enterprise. You do not need similar roles for IT admins or DBAs who will integrate and manage all aspects of Wyn. All such users fall under the "administrator" role.
Users in the "everyone" role are not granted any permissions by default. This is so that if any user who does not belong to a role accesses Wyn Enterprise, they will not be able to access any documents or resources.
If you are using a security provider, you must create roles identical to the user groups defined in your security provider.
4. Assign Permissions to Roles
Once your team defines roles in the Admin Portal, assign them the necessary permissions based on their needs within Wyn Enterprise.
For example, a DBA typically has control over a company datastore and has the right to query data from any given database. Such a role could be granted permissions to create data sources, semantic models, and datasets, and to query data directly from company databases. They could also create and distribute reports and dashboards.
Conversely, business users would not need such permissions relating to data, so their role could be restricted to only "create report" and "create dashboard" permissions.
5. Add Users to Their Defined Roles
After you set permissions for the different roles, add users to the Wyn Server, and assign them roles.
If you have configured a Security Provider with Wyn, you don't need to add and assign users manually. Wyn automatically recognizes them as a Wyn Server user and a member of their established user group.
Considering users in different groups may need access to the same documents, assign them to multiple roles when necessary. Wyn allows document sharing among users in the same role only.
For example, a DBA creates data sources and datasets. Their roles should include those of the workers who need access to these resources.
6. Share Documents and Resources from Wyn Portals
Once your team finalizes users and their respective roles, users can share documents and resources from the Document Portal and Resource Portal, respectively.
Wyn server administrators can specify role-based permissions on any document, to any role. Users share only their own created documents with other users in their roles.
Here are the different sharing options Wyn offers:
-
Read: View or fetch the content of a document with this permission. This action is the minimum permission allowed for documents such as Reports, Dashboards, Datasets, Images, and Themes.
-
Execute: Execute a query against the particular database and view the data in a report or dashboard. Similar to the "Read" permission, this is the minimum permission provided to data documents such as Data Sources and Semantic Models.
-
Execute/Create Dataset: In addition to retrieving the data in a report or dashboard, this option lets you create a new dataset (e.g., ad hoc query) and retrieve the data for a business need against a particular database.
-
Read/Write: Allow other users to edit and modify the content or layout of data resources and documents. Grant this permission to technical users who know when and how such modifications need to be made. Available for all documents.
When the user's role does not have permission to view certain documents, they won't be able to see it in the document portal when shared. A user with access to all dependent resources, including data sources and datasets, must grant at least "View" permissions to the role of the person in need of these dependent resources.
Moving Forward with Role-based Security
If you are an existing user of ActiveReports Server, role-based security in Wyn Enterprise provides increased protection thanks to new technologies and advanced data storage.
Embed Turnkey Dashboards & Reports
Wyn is a 100% web-based embedded BI platform that provides greater insight into your data.
Wyn offers built-in tools for report and dashboard creation, multi-tendency, data governance, security integration, and automated document distribution. All with an easy-to-use interface for self-service BI.