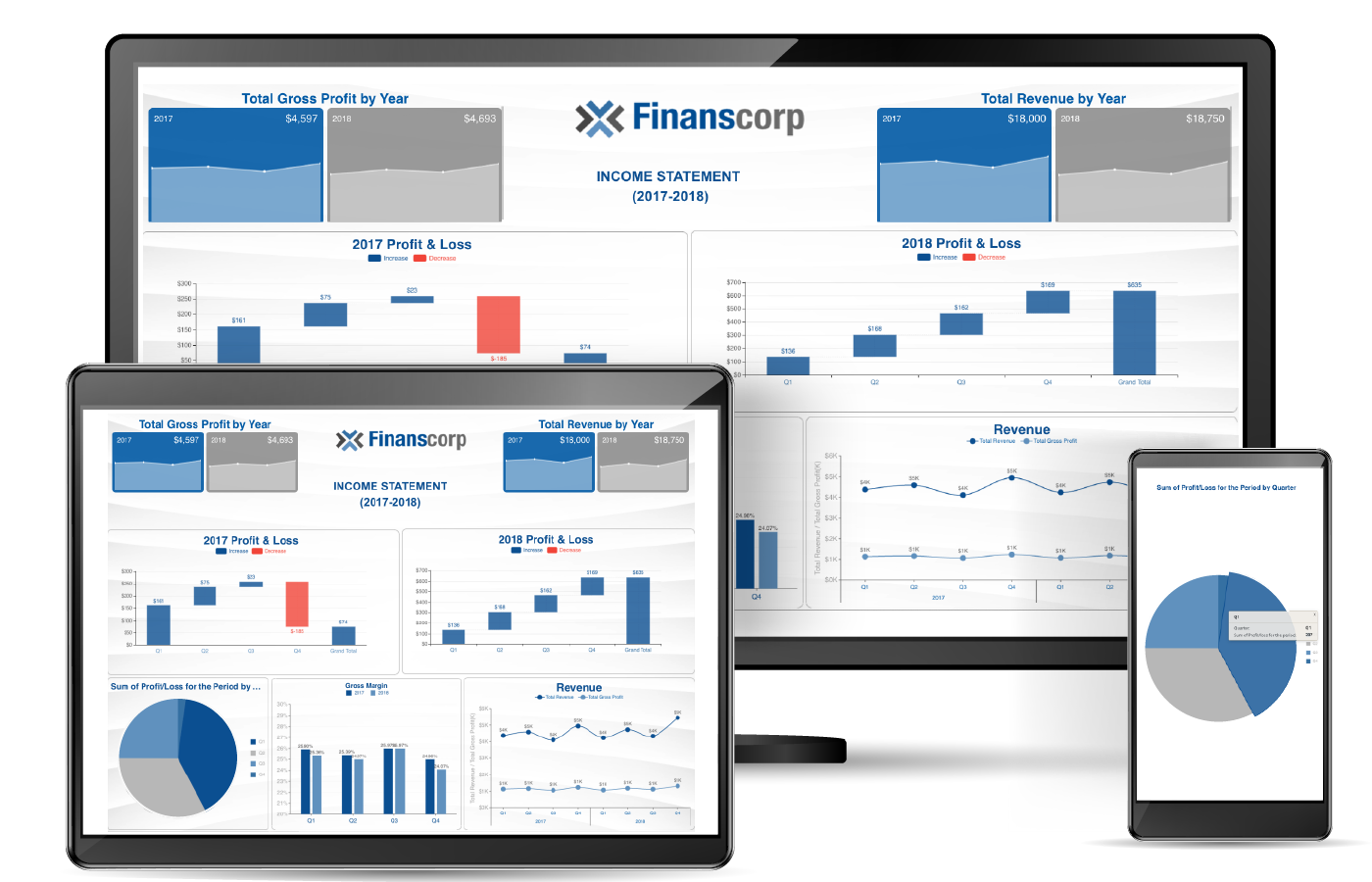
Work in a Secured Centralized Environment
The web-based admin portal allows you to configure your security rules so your IT team can easily manage roles, permissions, licenses, users, and security.
Role-based Permissions
Permission control for functionality and data access; user-context tracking for enhanced data access control.
Multi-tenant Support
Limit your tenant-specific data with the configurable role-based security and user-context definitions.
Extensible Security
Out-of-the-box extensible security module to customize to your security needs.
Extensible Security for Your Access Control Needs and Secure Business Intelligence
Configurable Role-based Security
Filter and segregate your data and limit your tenant-specific data with the configurable role-based security and user-context definitions.
Learn about role-based security in Wyn Enterprise.
Extensible Security with User Context
User contexts provide row-level data security in a document or database-level security for a data source.
User context acts as an additional layer of data security, extending the role-based security.
Granular Data Control for Additional Privacy
Each business has different authorization needs, data clearances, and business procedures.
Multi-level hierarchical security means granular data control that offers another layer of privacy.
Learn about role-based security in Wyn Enterprise.

Built-in End-to-end Security
Choose support for a variety of industry-standard protocols, including OAuth2, OpenID Connect, Active Directory, LDAP, and other federated security systems.
Or choose from Wyn’s built-in extensibility for the security module to integrate with virtually any authentication methodology or security system your organization is currently using.
Extend Wyn to talk to your Custom Security
Using the Custom Security Provider capabilities, you can extend Wyn Enterprise to talk to virtually any custom-built or off the shelf application-level security module using APIs.
Single Sign-On (SSO) Support
Wyn now supports SSO. A user can use a pre-authenticated environment and sign directly into Wyn for extra secure business intelligence. This helps to mitigate security risks and enhances the user experience.
See What our Customers are Saying:


































